##########################################################################
#The following information was not written by me. The networking section of the forum had little information so i #tought I should post some information.
##########################################################################
Credit goes to ----->
http://www.siteforinfotech.com/2012/11/internet-security-ip-security-ipsec.htmlInternet Security & IP Security (IPSec)
Internet Security is the securing web server and client (browser) from the possible attacks over the Wide Area Networks or Internet. Internet security is a type of Computer Security or the network Security. It includes mainly specific security protocols like IPSec (Internet Security Protocol), SSL (Secure Socket Layer) or TSL (Transport Layer Security). Internet Security also describes about PGP (Pretty Good Privacy) which is designed to create authenticated and confidential e-mails. It also discuss about Firewalls and Antivirus Programs.
# IP Security (IPSec)
IP Security (IPSec) is collection of protocols designed by Internet Engineering Task Force (IETF) to provide security for a packet at the network level. It helps to create authenticated and confidential packets for the IP layer. IPSec operates in one of the following two modes.
i) Transport Mode
In this mode, IPSec protects what is delivered from the transport layer to the network layer. i.e. the transport mode protects the network layer payload, the payload to be encapsulated in the network layer. This mode does not protect the IP header, i.e. it protects only the packet from the transport layer. In this mode, the IPSec header and trailer are added to the information coming from the transport layer. The IP header is added later. This mode is normally used when we need host-to-host protection of data. The sending host uses IPSec to authenticate and / or encrypt the payload delivered from the transport layer. The receiving host uses IPSec to check the authentication and / or decrypt the IP Packet and deliver it to the transport layer.
ii)
Tunnel Mode 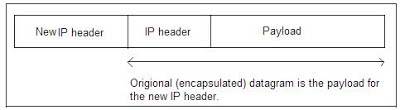
Tunneling or encapsulation is a common technique in packet-switched networks. It consists of wrapping a packet in a new one. That is, a new header is attached to the original packet. The entire original packet becomes the payload of the new one, as shown in Figure. In this mode, IPSec protects the entire IP Packet. It takes an IP packet including the header, applies IPSec security methods to the entire Packet, and then adds a new IP header. The new IP header has different information than the original IP Header.
In general, tunneling is used to carry traffic of one protocol over a network that does not support that protocol directly. For example, NetBIOS or IPX can be encapsulated in IP to carry it over a TCP/IP WAN link. In the case of IPSec, IP is tunneled through IP for a slightly different purpose: To provide total protection, including the header of the encapsulated Packet. Tunneling requires intermediate processing of the original packet while en-route. The destination specified in the outer header, usually and IPSec firewall of router, receives the tunneled packet, extracts the original packet, and sends it to the ultimate destination. The processing cost is compensated by the extra security. A notable advantage of IP tunneling is the possibility to exchange packets with private IP addresses between two intranets over the public Internet, which requires globally unique addresses.
The IPsec framework has three main components, Authentication Header(AH), Encapsulating Security Payload (ESP) and Internet Key Exchange (IKE).
Authentication Header (AH) AH is used to provide integrity and authentication of IP datagrams. Replay protection is also possible. Although its usage is optional, the replay protection service must be implemented by any IPsec compliant system. The services are connectionless, they work on a per-packet basis. AH is used in two modes, transport mode and tunnel mode.
Encapsulating Security Payload (ESP)

ESP is used to provide integrity check, authentication and encryption to IP datagrams. Optional replay protection is also possible. These services are connectionless, in that they operate on a per-packet basis. Encryption can be selected independently of other services. It is highly recommended that, if encryption is enabled, integrity check and authentication be turned on. Like AH, ESP can be used in two ways: Transport mode and tunnel mode.
Internet Key Exchange Protocol (IKE)
The internet Key Exchange (IKE) framework, previously referred to as ISAKMP/Oakley, supports automated negotiation of security Associations, and automated generation and refresh of cryptographic keys. The ability to perform these functions with little or no manual configuration of machines is a critical element to any enterprise-scale IPsec deployment. Internet security association and key management protocol (ISAKMP) is a framework that defines the management of security associations (negotiable, modify, delete) and keys, and it also defines the payloads for exchanging key generation and authentication data. Internet Key exchange (IKE) is a protocol that uses parts of ISAKMP and the Oakley and SKEME key exchange protocols to provide management of keys and security associations for the IPsec AH and ESP protocols and ISAKMP itself.


