IntroductionThis tutorial will cover in detail the difference between different types of malware, since most people call everything they see a virus, There are 3 "main" types of malware, a Virus, A Worm and a Trojan, each of those malware break into other sub sections like, A backdoor caused by a trojan (Trojan.backdoor), Email worm(Worm.Email) and so on. ill try to cover in detail each type.
MalwareShort for Malicious Software, a program that is created to potentially harm your computer in anyway. such as stealing data, corrupting data, stealing money and using your own computer against you or other people. Malware is a Trojan, a virus or a worm.
PayloadA payload is the "cargo" that the malware unloads on exectuion or a spesific date, it could be anything. most payloads corrupt data, connect the user to a botnet or just make the computer unusable. examples: Worm.Email.Gruel, Virus.CIH, Trojan.backdoor.darkcomet
VirusMuch like a biological virus, a computer virus attempts to infect hosts by injecting its code to other files, in this way the virus replicates itself thus executing each time the user runs an infected file, unlike other malware the virus needs human existence to work, first a user must activate the infecting file and then launch other programs each to for the virus to infect, if the user doesn't press anything the virus wont run unless the files the virus infected are already running, each virus has a payload that executes on a specific date or instantly. Although viruses need humans to live it is a very very dangerous malware, when game companies released disks infected with the CIH for example(Yeah it happened) a lot of users lost their data because of the malicious payload the virus had. Over writing the Master Boot record with zeros.
Marco viruses who used Microsoft Office exploits email themselves and destroy computers, Like the Mellisa macro virus who was email and believed to have porn passwords. on execution the virus would corrupt data making the computer un-booteble. A virus payload could also open random files and folders and open porn websites just too annoy the user.
WormA computer worm also is a self replicating program that attempts to spread itself using that replication, unlike a virus worms do not modify files and destroy them, worms do not need human existence to work, once a worm has run it can function alone. Worms consume a lot of bandwith because they attempt to spread using the network, worms often install backdoors in the computer to connect the computer to a botnet or a RAT. worms often delete files in the system to remain undetected or destroy the computer.The Gruel worm for example arrived in an email with a very malicious payload, once activated it would mass email itself and then remove files from System32, opening random files, websites, constantly opening message boxes, creating a lot of errors that cause Blue Screens of death, restoring the computer to a normal state after the infection of the Gruel worm is almost impossible.
Another example of a worm is the MyDoom worm, on execution the payload would mass email itself to other computers, open a backdoor and then launch a DDOS attack on
www.sco.com. the email form would look like this:"andy; I'm just doing my job, nothing personal, sorry".
Later the DoomJuice worm exploited backdoors that were opened in computers by MyDoom to connect the computer to a botnet.
TrojanBefore we talk about the Trojan i want to tell you guys a little story, Long time ago two countries had a war, The Greeks had decided to give a small present to the City of Troy to end the war, so they brought a big wooden horse as a present to the people of Troy, once the present entered the big city, who was heavily protected with men and huge walls, they opened the horse and a huge amount of Greek soldiers raided the city, destroying and burning it to the ground.
A trojan arrives as a legitimate program, it would appear like a regular program, an Anti-Virus, A windows update or even a hacking tool, on execution it would drop a very malicious payload, it could be anything, from annoying the user and connecting him to a botnet without hes acknowledgement or encrypting the users files and asking for a ransom for decrpytion(CryptoLocker,CryptoBit). A trojan is a Keylogger, A trojan is a backdoor.
The difference between other malware and a trojan is that a Trojan doesnt replicate itself or attempt to spread itself or need human action to exist.(besides from executing the infected file)
A very dangerous trojan was the CryptoLocker, who encrypted files on execution and demanded a 300 dollar ransom to decrypt the files.
Ransomware or Scareware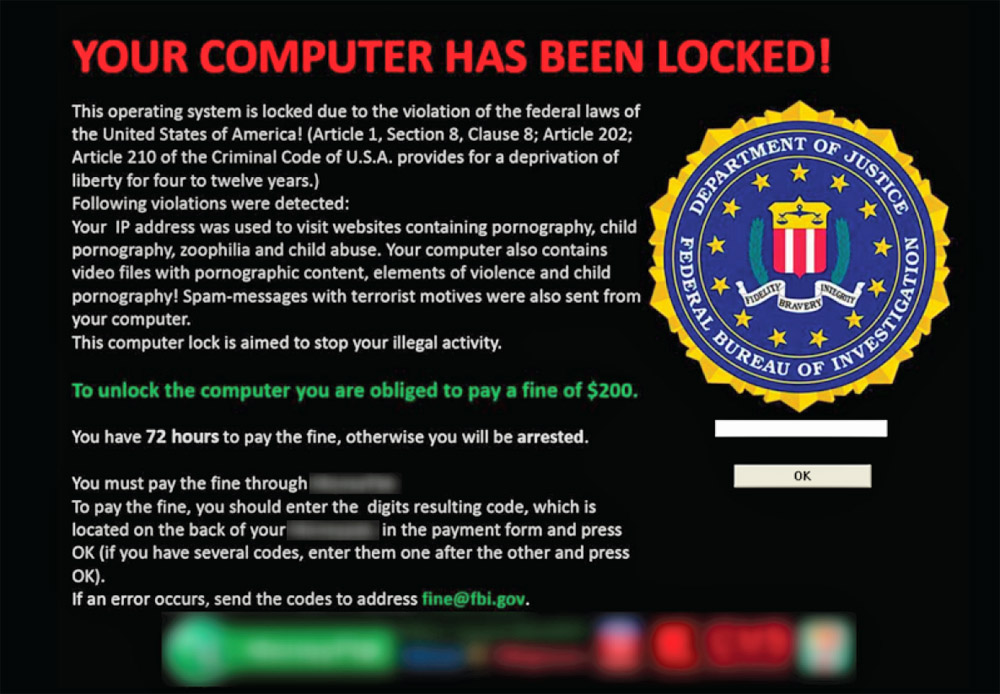
The big pathological liar of all malware, the Ransomware or the Scareware. The names are given for obvious reasons.. Scaring the victim and asking for a ransom. Ransomware is usually classified as a trojan. The ransomware will usually arrive as a legitimate program, downloadable porn, new updates, hacking tools. Anything, on execution it will drop a very malicious payload which "locks" your computer and asks for a ransom sometimes lying, like you can see in the picture or sometimes being honest and true like the CryptoLocker. Admitting that the program encrypted your files and if you want them back you need to pay a ransom. Ransomware can be also downloaded by force from Drive-By Downloads. Some ransomware can be really easy to remove, for example if it modifies the Windows Shell or Add registry keys to boot up with the OS but if the malware over-writes the Master Boot Record, you could be in a jam.
Ransomware is also responsible for suicide - news.softpedia.com/news/Romanian-Man-Commits-Suicide-After-Police-Ransomware-Tells-Him-He-Must-Pay-Fine-431882.shtml
If you are having problems with Ransomware you can always watch Rogueamp videos or contact him -
https://www.youtube.com/channel/UCzuKOJtTTVCxWgi1SM8Kg6gBackdoorA Backdoor is a method of bypassing a computers security system(or a servers) and gaining access to it without permission and remaining undetected.
Most of the backdoors carry the payload of a RAT or a botnet in these days although back in the days the MyDoom Worm installed a backdoor which allowed to create DDOS attacks.
A Backdoor webshell is another example where the attacked used PHP code format to gain remote control of computers.
A backdoor could allow a lot of functions as it takes over the computer, such as keylogging, browser hijacking, browser stealing, File Transfer, File Execution and so on, but a backdoor could be a trojan a virus and a worm.
DownloaderA Downloader is a type of malware that is useally an addition to the originaly downloaded malware but it could work as a standalone, a Downloader downloads additional malware to the system.
The "Download And Execute" Option in botnets and RATS can be also labeled as a downloader but in cases such as in a Conflicker infection, it would update itself to a newer variant of itself each time.
Pictures and shit
- Gruel worm

- CrpytoLocker

- ILOVEYOUWORM arriving in an email, on execution it would mass email itself and then overwrite un-critical files on the computer, due to its easy modified nature, new variants of the worm over written critical system files.
http://www.youtube.com/watch?v=3GAMFERRs1k- LOVEYOU trojan who deleted critical system files as a payload after it stressed the user.
TODO List:
Ransomwarelauncher
backdoordownloaderrootkit
rogue
spam-sending malware
spyware