Today I'm going to show you how to create an encrypted hidden container volume using Truecrypt.
What is a hidden volume?
Lets say that you have some very sensitive files that is encrypted on your computer and someone (roommate, government, someone with a gun) wants to look at those files. However, you do not want to release those files but instead show them a different set of files that are similar (or fake). You then can release a different password to them that will only show them the other non-sensitive files keeping the real files safe from exposure.
So how does this work?
We are basically creating a virtual hard drive that has two parts, a outer volume and hidden volume. Each volume will have a different password, and you may only access that volume with the matching password.
+++++++++++++++++++++++++++++++++++++++++++++++
+ +
+ +
+ Outer Volume Hidden Volume +
+ Password:123456 Password:654321
+ +
+++++++++++++++++++++++++++++++++++++++++++++++
To get started download your copy of TrueCrypt here:
http://www.truecrypt.org/ and install it on your computer.
Once installed, open the volume manager:
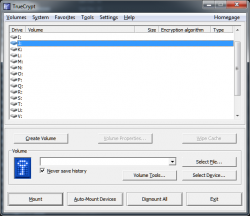
Then click on
Create Volume, this will start the wizard.

The first step is to select what kind of volume you want to create. You can use this program to encrypt an entire hard drive or just a small container volume. Today we are going to select "Create an encrypted file container" then click
next.
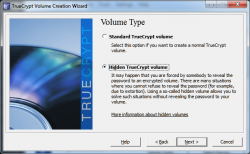
For volume type click on "Hidden TrueCrypt volume", then click
next.
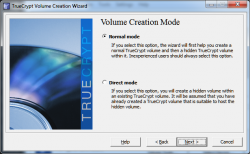
For the creation mode we will be creating a new volume so click on "Normal Mode", then click
next.
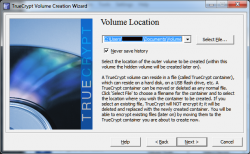
For this step we are going to name and save the file. You can save the container file anywhere on the hard drive. Once finished click
next.
Now we are going to create the outer volume.
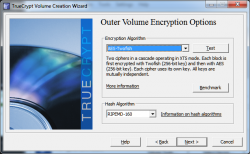
For this step you can choose any encryption algorithm that best suits you, for this demo I'll choose AES-TwoFish, then click
next.
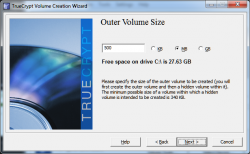
Now for this step, depending on how much hard drive space that you have or the size of the files that you want to have encrypted, you can make the volume as big or small as you want. Keep in mind that you would want to use an 50/50 approach when creating the volumes. For example, if you create an volume that is 100 GB use 50 GB or the outer volume and 50GB for the hidden volume. For this demo I'll create a volume with 500MB of space. Once finished, click
next.
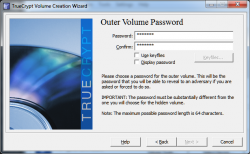
Now create a password that will be used to access the outer volume. You can choose a weak password since this is not the hidden volume.
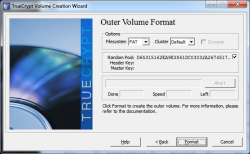
Next we are going to format the volume using a
FAT filesystem, then click on
format.
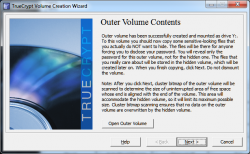
Once that is complete, click
next.

Like I said before we are going to an 50/50 approach. So, we are going to make the hidden volume half the size of the whole volume. Then click
next.
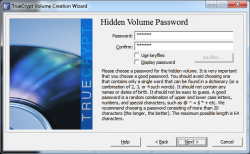
Now it's time to create the password for the hidden volume. MAKE SURE YOU USE A STRONG PASSWORD!!! For this demo I'm using "654321."

Once you finish creating the hidden volume exit out the wizard to go back the volume manager. Next, click on
the Select File... button then open the container file at the location where you saved it. Then click on the
Mount button
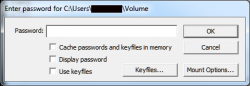
A pop will show up asking for the password, but we are going to click on
Mount Options... first.
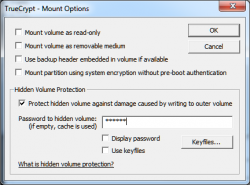
In the mount options menu check the box "Protect hidden volume against damage caused by writing to outer volume." Then type in your password for the hidden volume. This option will prevent any information from begin overwritten on the hidden volume by anyone (system or user) writing files on the outer volume.
Then click
ok.
Then type in your password for the outer volume and click
ok. You now opened the outer volume. You can store some files non-sensitive here. Once finished go back to the volume manager and dismount the volume.
Then select the container file again and mount the drive. When the pop-up prompts you for a password, enter the password that you created for the hidden volume. Now you have access the the hidden volume.



















