Using Excel for Macro Malware DeobfuscationAlthough I want to write only tutorials that require free software, it is in some cases not possible. MS Office malware is such a case. VBA macros are not used on free products like Libre Office (it uses Libre Office Basic). Nor can you execute any VBA-based Macro malware in a dynamic analysis system without MS Office installed. So in this case, I make an exception.
Often you will get Macro Malware that is obfuscated; and if you don't have MS Office on your dynamic analysis machine, you must rely on static analysis to find out what the malware does.
If you don't have MS Office at all, you will have to rewrite parts of the macro code to another language to deobfuscate. This is more tedious, but it is just the way it is.
Download the following sample:
macromalware.zipThis is life malware!
Run this sample only in a properly secured dynamic analysis VM!The password is "infected".
Take a look at the Macro code. The author of the code was so friendly to leave some comments that help you to see what is going on. But what does this code do?
As you may know by now, Macro trojans are in almost all cases either droppers or downloaders. This malware imports a function called
URLDownloadToFileAPrivate Declare PtrSafe Function IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm02 Lib "urlmon" Alias "URLDownloadToFileA" _We can safely assume that this is a downloader.
Take a look at the rest of the macro code. Some lines that should immediately catch your eye are these (I used olevba for extraction, if you used something different, the line numbers may not match)
Line 59:IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm15 = "feiwfiewmfiew fmewifmewimfiew fmewifmewimfgiewmfgi mmdemwioqwqjjfqf fewmfoewgoewgfew Umbrella HBjhbhjkshdjkhJNggg GjHgggJkmNjh 4rff4r43 GjNghJGjhJggggJh ggJnggfgHfgHdfG dfGdfGHHfGHH dDFCdFGBHVBhGjijok ghnfVBFGRTYJh fCvFgyhBgHHhFvB .exe fewrfwegwfewfewfwefwef"This contains the string .exe and looks like a list of possible file names.
Line 72:IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm24 = IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm10 & IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm10 & "" & "C:\Users\" & IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm09 & "\AppData\Roaming" & Split(IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm16)(5) & IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm14 + IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm11Concatenated strings and parts of these are system pathes. Maybe this shows where the downloaded malware is saved to.
Line 100:'check whether running encryption or decryption (flagged by presence of "xxx" at start of IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm31):This is a valueable comment. This line is within a decryption/encryption routine (also indicated by use of Xor, interestingly the author suggests in the comments to avoid use of Chr). I immediately checked where I can find strings with xxx (make a text search, CTRL + F). Alternatively check where you find calls to the decryption routine (search for the name of the routine or in Notepad++ click on it so it gets highlighted). I found these interesting lines:
Line 67:IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm19 = IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm21("xxx*/6+|vo*!6rlp6$1%:6*664<'@p*/=67!$%)p5%/o-qv�����:&p#j!ltxr9r:mos@ux$:u<m@rj#i$cs<qmxv2))8///+o7/8p@:@", "AZAZ")Line 68:Dim IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm20 As String: IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm20 = IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm21("xxxGAQDYDH C\W^^", 1331)Both of these lines call the encryption/decryption subroutine. That means they have something interesting to hide. Let's decrypt the strings.
We could of course use Python or any other language to rewrite the decryption routine, but that is more work than necessary. Often it is easier to stick with the language that we already have, so we can just copy the code.
In Excel open the
Developer tab. You may have to turn it on first.
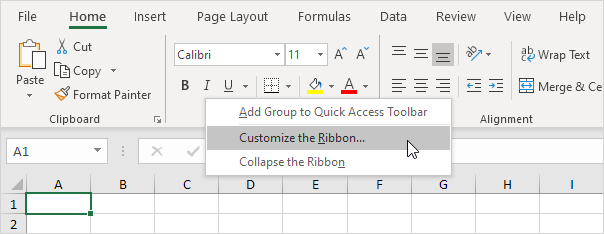
Under
Customize the Ribbon, on the right side of the dialog box, select Main tabs (if necessary).
Check the
Developer check box.
Click
OK.
Now you should see the Developer tab. Click it.
Press the
Insert button choose the
Command Button, the click somewhere on the Excel sheet to place it.
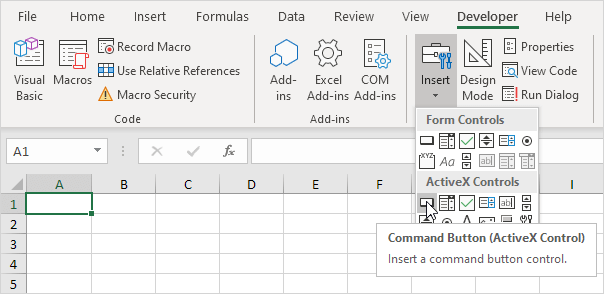
Right-click on the command button and click
View Code. This will open up the Macro Editor.
Copy the decryption routine of the macro malware into the code window.
Note: You must be 100% sure that the copied code is safe to run, if you don't use a safe environment for it.Into the
CommandButton1_Click routine you copy the call to the decryption routine that you also find in Line 67 of the Macro malware. It will look as follows:
Private Sub CommandButton1_Click()
Range("A10").Value = IKkiie40f432innMNMMMdfnewifnMMIeninfwfewdwdwqm21("xxxGAQDYDH C\W^^", 1331)
End SubScreenshot:

This code will save the decrypted string to the field A10 of the Excel sheet. Now if you press the command button on your Excel sheet or the run button in the code editor, it will print out the decrypted string for you.
The result will look as follows:

Try the same with the other string and you will find out were the macro downloads files from.